
Introduction
Code on Github: Elasticsearch and Beats
We will setup Auditbeat with Elasticsearch and Kibana. If you do not have Elasticsearch and Kibana set up yet, then follow these instructions.
This video assumes you are using Publicly Signed Certificates. If you are using Self Signed Certificates, go here TBD.
Requirements
A running instance of Elasticsearch and Kibana.
An instance of another Ubuntu 20.04 server running any kind of service.
Steps
Step 1 - Download Auditbeat [01:12]
On the Ubuntu machine that will run auditbeat, run these commands to download dependencies:
wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | sudo gpg --dearmor -o /usr/share/keyrings/elasticsearch-keyring.gpg;
echo 'deb [signed-by=/usr/share/keyrings/elasticsearch-keyring.gpg] https://artifacts.elastic.co/packages/8.x/apt stable main' | sudo tee /etc/apt/sources.list.d/elastic-8.x.list;
sudo apt-get install -y apt-transport-https;
apt-get install -y auditbeat;
Step 2 - Configure Auditbeat [02:14]
Edit these fields for the /etc/auditbeat/auditbeat.yml
- module: system
state.period: 2m
setup.dashboards.enabled: true
setup.kibana:
host: "https://<kibana-domain>:<kibana-port>"
output.elasticsearch:
hosts: ["<elasticsearch-domain>:<elasticsearch-port>"]
protocol: "https"
username: "elastic"
password: "<your elastic password>"
Completed auditbeat.yml can be found here
IMPORTANT - we are using the elastic super user for the initial set up and configuration. We will downgrade the privileges later.
Then test your configuration with these commands:
/usr/share/auditbeat/bin/auditbeat test config -c /etc/auditbeat/auditbeat.yml --path.data /var/lib/auditbeat --path.home /usr/share/auditbeat
/usr/share/auditbeat/bin/auditbeat test output -c /etc/auditbeat/auditbeat.yml --path.data /var/lib/auditbeat --path.home /usr/share/auditbeat
You should see something like this:
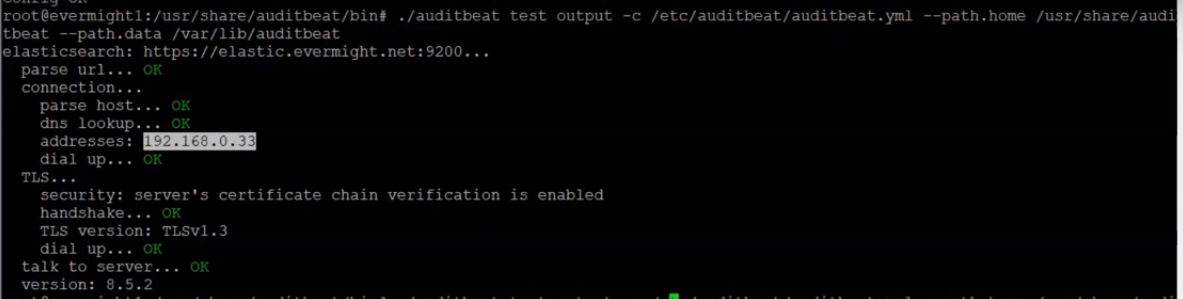 Verify auditbeat configuration
Verify auditbeat configuration
Step 3 - Setup Auditbeat [10:22]
Now run this command to set up auditbeat datastreams and views in Elasticsearch and Kibana:
/usr/share/auditbeat/bin/auditbeat setup -c /etc/auditbeat/auditbeat.yml --path.data /var/lib/auditbeat --path.home /usr/share/auditbeat
Once the command finishes, go to Kibana Menu and visit Dashboard to see many pre-made dashboards.
Step 4 - Create a Publishing User [11:42]
Create Role
In Kibana, go to Stack Management > Roles > Create role. Then fill out these fields:
Role name: auditbeat-publisher
Cluster privileges: monitor, read_ilm
Indices: auditbeat-*
Privileges: create_doc
Create User
In Kibana, go to Stack Management > Users > Create user. Then fill out these fields:
Username: auditbeat-publisher
Full name: auditbeat-publisher
Email address: anything@anything.com
Password: anything
Roles: auditbeat-publisher, editor
Create API Key for User
In Kibana, go to Dev Tools > Console. Then run this command:
POST /_security/api_key/grant
{
"grant_type": "password",
"username": "auditbeat-publisher",
"password": "anything",
"api_key": {
"name": "auditbeat-publisher"
}
}
This should produce a result like:
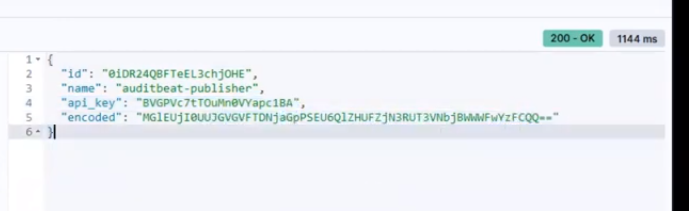 Auditbeat user token
Auditbeat user token
Edit the /etc/auditbeat/auditbeat.yml by commenting out the elastic username and password and enabling the api_key like so:
output.elasticsearch:
...etc...
api_key: "${ES_API_KEY}"
#username: "elastic"
#password: ""
...etc...
We will be using the auditbeat keystore to load secrets for run time. Now run this command to set the ES_API_KEY keystore variable:
/usr/share/auditbeat/bin/auditbeat keystore add ES_API_KEY -c /etc/auditbeat/auditbeat.yml --path.data /var/lib/auditbeat --path.home /usr/share/auditbeat
Press enter and when prompted, paste in <id>:<api_key> where the <id> and the <api_key> are the values from the user token response you got previously.
Step 5 - Run Auditbeat [19:22]
systemctl enable auditbeat.service;
systemctl start auditbeat.service;
In a moment, you should start seeing results in Kibana in either Discover, Observability, Stack Management > Index Management > Datastream, Dashboard > Select an Auditbeat dashboard.
