
Introduction
We will install Elasticsearch and Kibana and secure it with self signed SSL certificates.
Requirements
In the video, we used two instances of Ubuntu 20.04 running on a VM in a cloud service.
We assume you also have A Records in your DNS that map one domain to the Elasticsearch VM and one domain to the Kibana VM. For our demonstration below, we will use elastic.evermight.net and kibana.evermight.net.
Steps
Step 1 - Update Ubuntu [02:30]
Both Ubuntu installations are brand new. We update the distribution as well as install some tools we typically use on both machinese.
apt-get update && apt dist-upgrade -y && apt-get install -y vim curl gnupg gpg
Step 2 - Install Elasticsearch [02:50]
Both Ubuntu installations needs these dependencies, so run these commands on both:
wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | sudo gpg --dearmor -o /usr/share/keyrings/elasticsearch-keyring.gpg;
echo 'deb [signed-by=/usr/share/keyrings/elasticsearch-keyring.gpg] https://artifacts.elastic.co/packages/8.x/apt stable main' | sudo tee /etc/apt/sources.list.d/elastic-8.x.list;
apt-get install -y apt-transport-https;
apt-get install -y elasticsearch;
When installation is complete, make sure you write down the password.
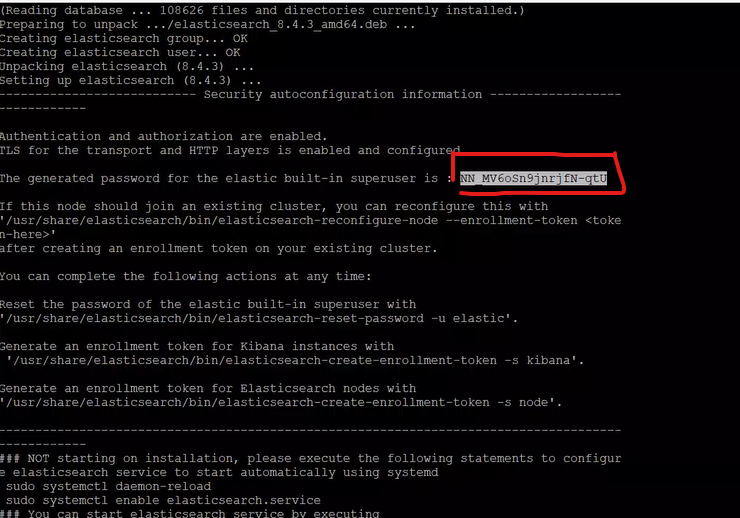
Step 3 - Make Self Signed Certificate for Elasticsearch [04:50]
Let's make self-signed SSL certificates for elastic.evermight.net and kibana.evermight.net.
Go to the elastic.evermight.net shell.
Make the certificate authority with this command:
/usr/share/elasticsearch/bin/elasticsearch-certutil ca --pem --out /etc/elasticsearch/certs/ca.zip
cd /etc/elasticsearch/certs/
unzip ca.zip
Now let's make a self-signed certificate for elastic.evermight.net and sign it with our ca.crt:
/usr/share/elasticsearch/bin/elasticsearch-certutil cert \
--out /etc/elasticsearch/certs/elastic.zip \
--name elastic \
--ca-cert /etc/elasticsearch/certs/ca/ca.crt \
--ca-key /etc/elasticsearch/certs/ca/ca.key \
--dns elastic.evermight.net \
--pem;
cd /etc/elasticsearch/certs/;
unzip elastic.zip
Optionally, if you are using IP address as well, you can pass in the --ip option and state your IP address.
Step 4 - Configure Elasticsearch [03:50]
Edit elasticsearch.yml
Go to the /etc/elasticsearch/elasticsearch.yml file. Edit the following fields:
...etc...
cluster.name: <anything you want>
...etc...
network.host: elastic.evermight.net
...etc...
http.port: 9200
...etc...
xpack.security.http.ssl:
enabled: true
key: certs/elastic/elastickey.
certificate: certs/elastic/elastic.crt
certificate_authorities: certs/ca/ca.crt
...etc...
Change ownership
chown -R elasticsearch:elasticsearch /etc/elasticsearch
Step 5 - Start Elasticsearch [12:45]
Start elasticsearch with these commands:
systemctl enable elasticsearch;
systemctl start elasticsearch;
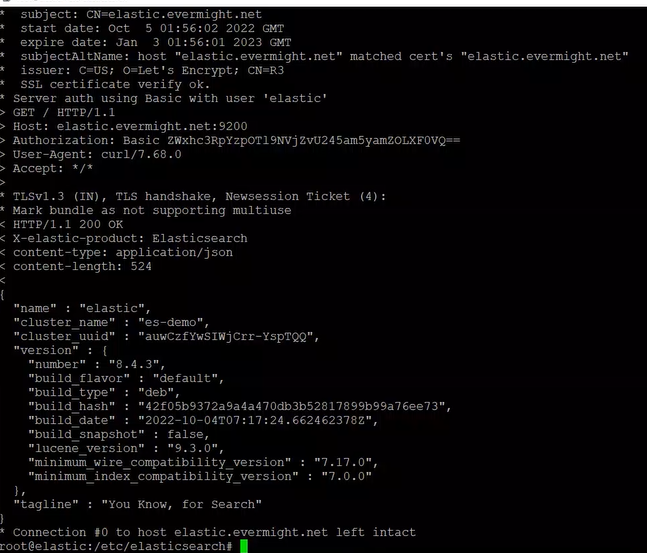
Confirm elasticsearch is working with this command:
curl -X GET -u elastic:<password from step 2> https://elastic.evermight.net:9200 --cacert /etc/elasticsearc/cert/ca/ca.crt
And you should see something like this:
Step 6 - Install Kibana [16:10]
Run this command on the kibana.evermight.net machine:
wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | sudo gpg --dearmor -o /usr/share/keyrings/elasticsearch-keyring.gpg;
echo 'deb [signed-by=/usr/share/keyrings/elasticsearch-keyring.gpg] https://artifacts.elastic.co/packages/8.x/apt stable main' | sudo tee /etc/apt/sources.list.d/elastic-8.x.list;
apt-get install -y apt-transport-https;
apt-get install -y kibana;
Step 7 - Make Self-Signed Certificate for Kibana
Now let's make a self-signed certificate for kibana.evermight.net and sign it with our ca.crt. Go to your elastic.evermight.net machine and run this command:
/usr/share/elasticsearch/bin/elasticsearch-certutil cert \
--out /etc/elasticsearch/certs/kibana.zip \
--name elastic \
--ca-cert /etc/elasticsearch/certs/ca/ca.crt \
--ca-key /etc/elasticsearch/certs/ca/ca.key \
--dns kibana.evermight.net \
--pem;
cd /etc/elasticsearch/certs/;
unzip kibana.zip
We will copy the /etc/elasticsearch/certs/kibana/* over to the kibana.evermight.net shortly.
Step 8 - Configure Kibana [15:26]
Copy over SSL certificates:
Go to your kibana.evermight.net server and run this command:
mkdir /etc/kibana/certs/kibana
Then copy your SSL certificates from Step 7 into the directory above.
Edit kibana.yml
Go to the /etc/kibana/kibana.yml file. Edit the following fields:
server.port: 5601
server.host: 0.0.0.0
server.publicBaseUrl: "https://kibana.evermight.net:5601"
server.ssl.enabled: true
server.ssl.key: /etc/kibana/certs/kibana/kibana.key
server.ssl.certificate: /etc/kibana/certs/kibana/kibana.crt
server.ssl.certificateAuthorities: /etc/kibana/certs/ca/ca.crt
elasticsearch.hosts: ["https://elastic.evermight.net:9200"]
elasticsearch.ssl.verificationMode: full
elasticsearch.ssl.certificateAuthorities: ["/etc/kibana/certs/ca/ca.crt"]
Create Service Token
Run this command on the Elasticsearch server:
/usr/share/elasticsearch/bin/elasticsearch-service-tokens create elastic/kibana kibana-token
chown -R elasticsearch:elasticsearch /etc/elasticsearch
Copy the token that you see.
Run this command on the Kibana server:
/usr/share/kibana/bin/kibana add elasticsearch.serviceAccountToken
Paste in the token after the prompt.
Step 9 - Start Kibana [27:50]
systemctl enable kibana;
systemctl start kibana;
Now you can visit https://kibana.evermight.net:5601/ and login with elastic and the password from step 3.
